A way to help you manage your Psono accounts
Remembering tons of passwords for an ever-growing number of online accounts and services is not an easy feat. Counting this reason and a lot of others it was decided to use a secure password manager software. Psono is a secure password manager that was first launched in 2017, an open-source that provides end-to-end encryption that ensures only end-users ever have access to the keys needed to access the encrypted passwords stored on its servers.
When installing psono, we have our client UI(user interface) but the admin user can also have a feature that will help us monitor and manage all the users for our psono is Admin Panel.
The following sections describe an overall view of Psono Admin Panel.
Dashboard
The dashboard may be described as the "first-sight" appearance of the psono panel UI. The first image shows the "health check" of the database accessibility, database synchronization, and time synchronization. In other words, we can see if the database is reachable, if there are any pending database migrations, and if the server time is correct. In our case we have everything set up and running so the 'health check' section is in green.
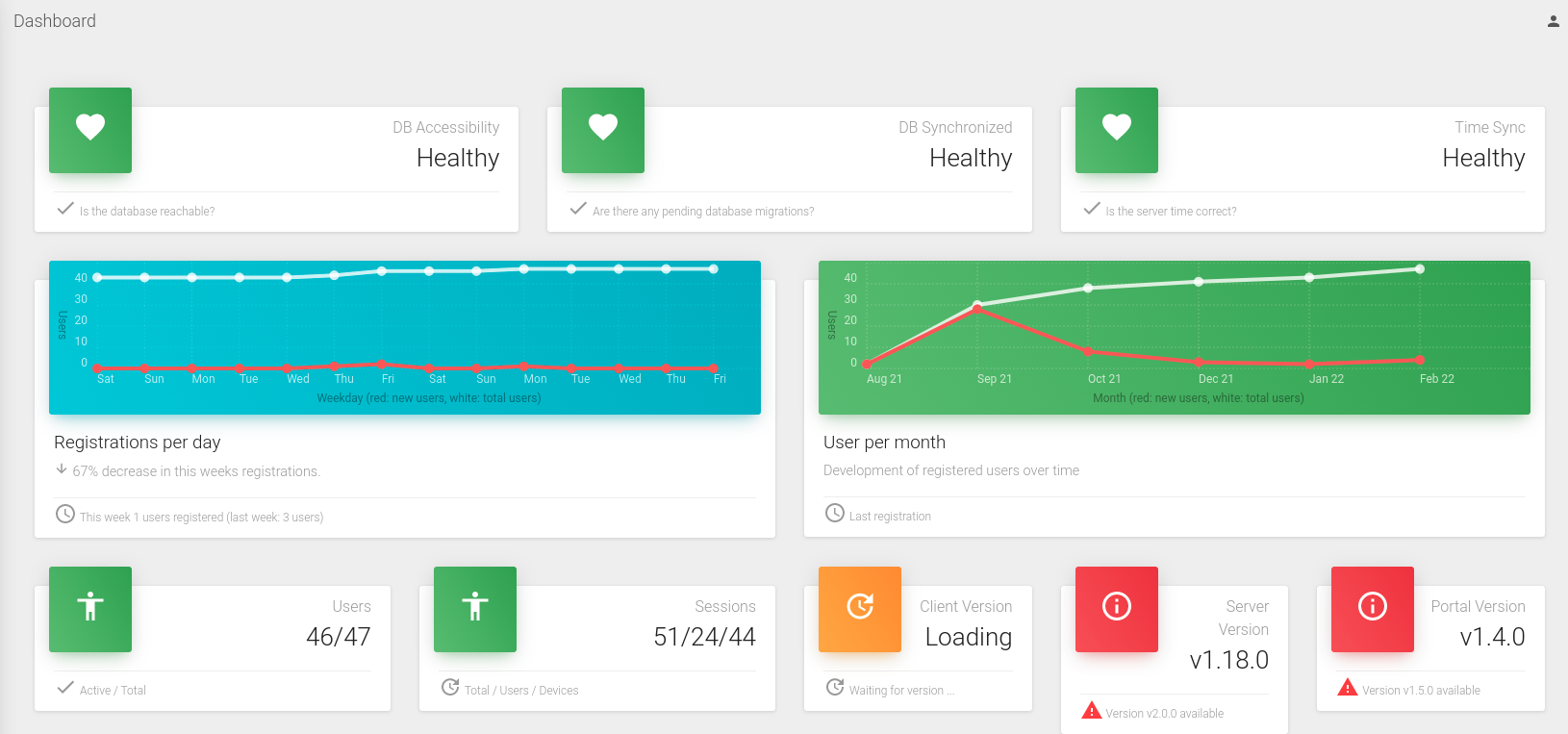
We can see the statistics about the registration per day and the users per month. Next, we can see the total users and the sessions (in our case we have 46 active users, 51 sessions from 24 users in 44 devices). We can check the Client, Server, and Portal versions for our psono also.
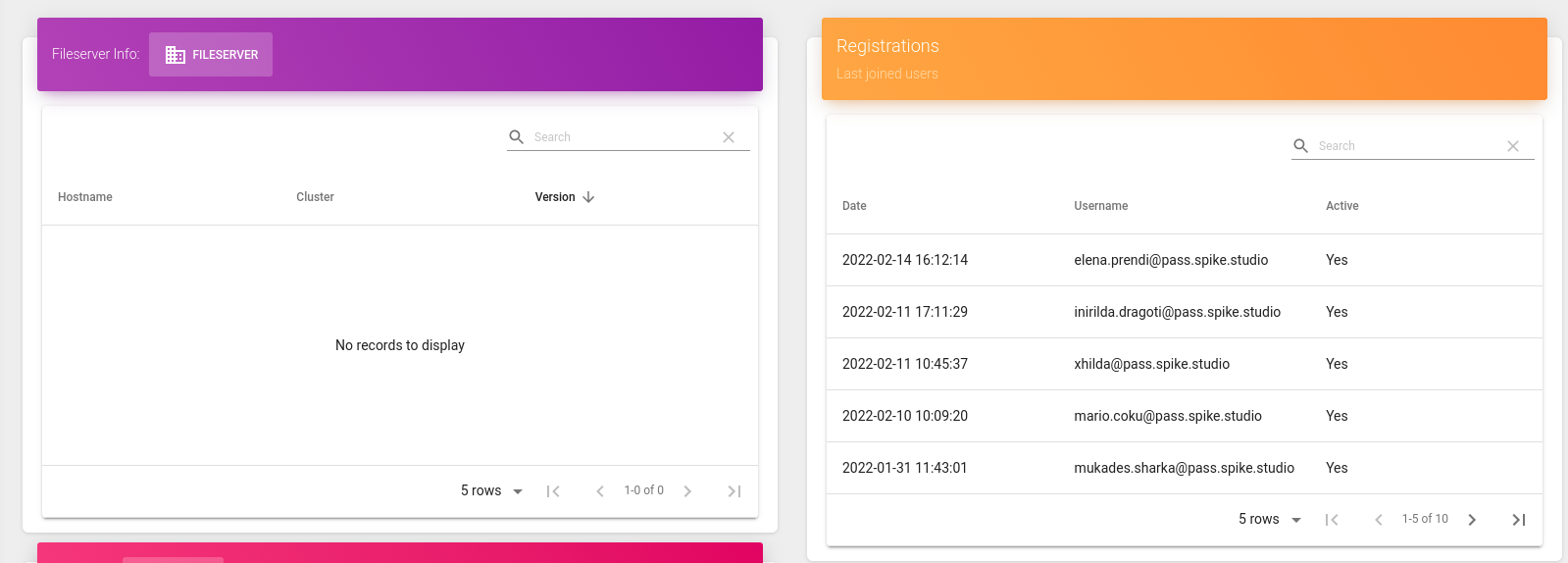
In the second figure, you can check the information about the file server and the registration of the users with the respective date, username, and status.
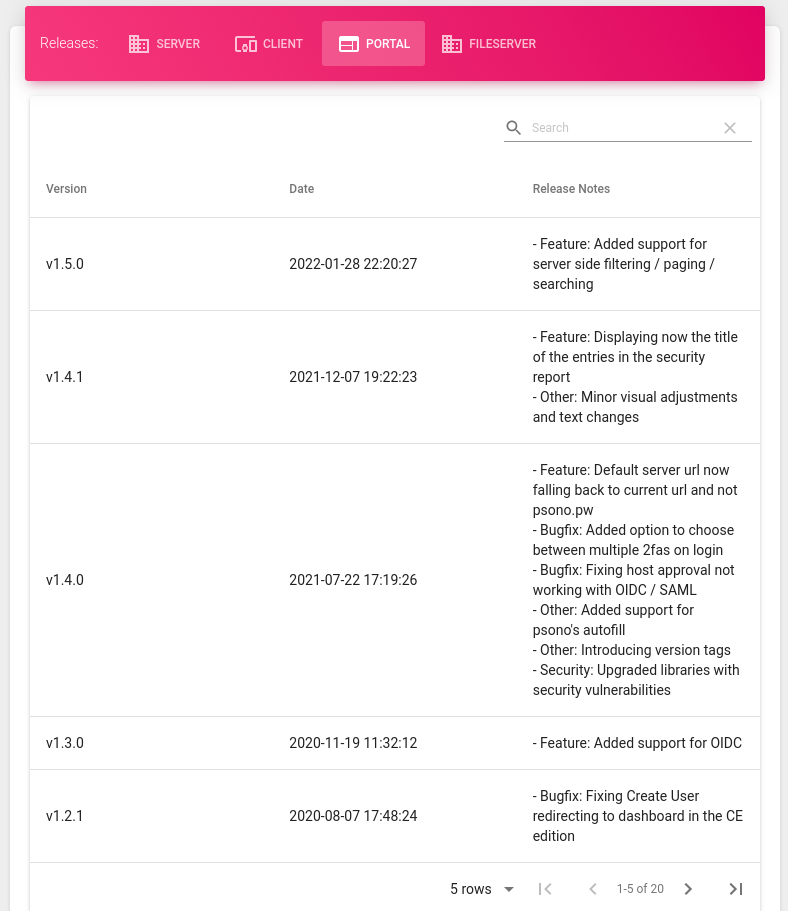
The last feature of the dashboard is the release table, which shows information about the latest releases of the server, client, portal, and fileserver with the details of each newly released version and the date of the launch.
Users
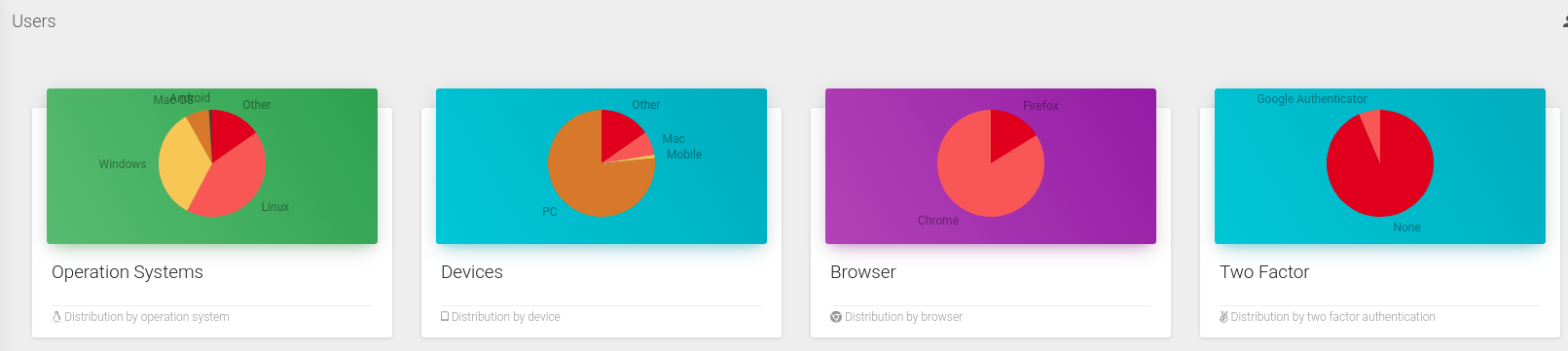
In the User section, we can see four pie charts at the top of the page:
- the type of operating systems that are used by our registered users (showed on a pie chart defined as "Distribution by operation system"). In our case we have a distribution of the operating systems mostly Linux and Windows, the other percentage is MAC, a few of them use Android and there are users that are using other OS while accessing Psono.
- the distribution by device, again shown by a pie chart- on the image that we have attached below
- the distribution by browsers (in our case most of the users do use chrome and a few of them use firefox)
- the last pie chart shows what is the percentage of users that have activated the two-factor authentication for their psono account.
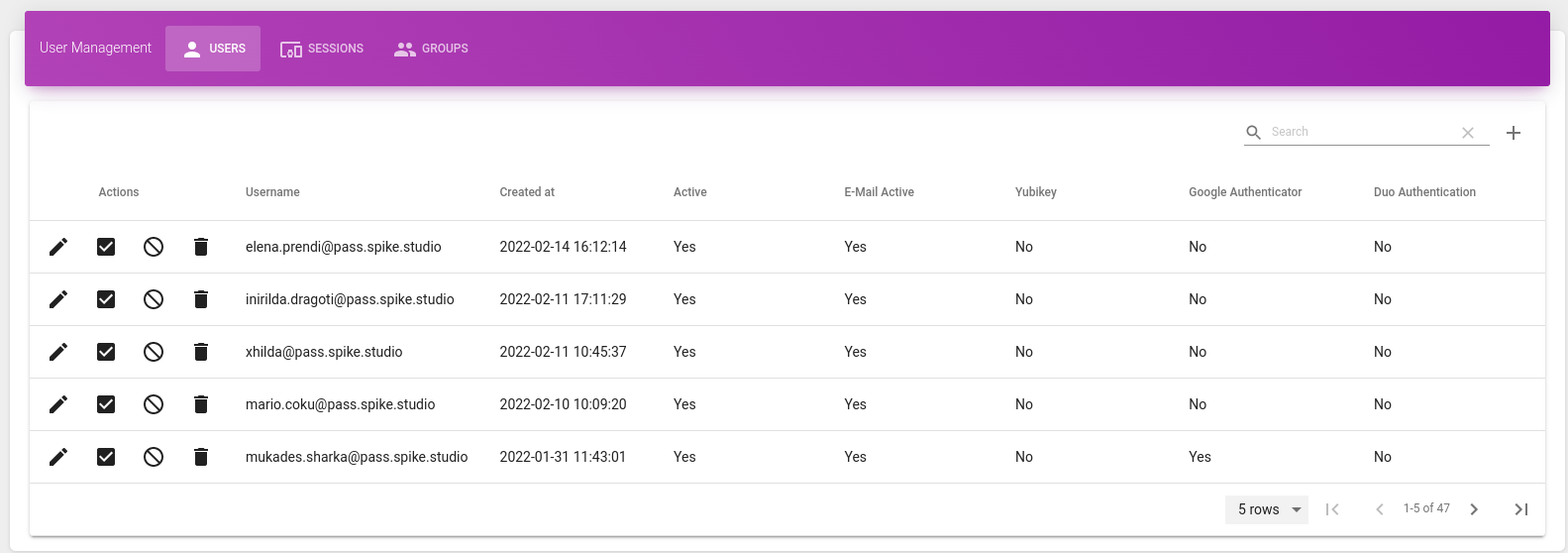
At the bottom of the page, we have the user management table. We can see there:
- the user table of all the users with the respective date when it was created, if it is active and has an email address, google authenticator, etc. There we can also edit or delete a user in case we want to.
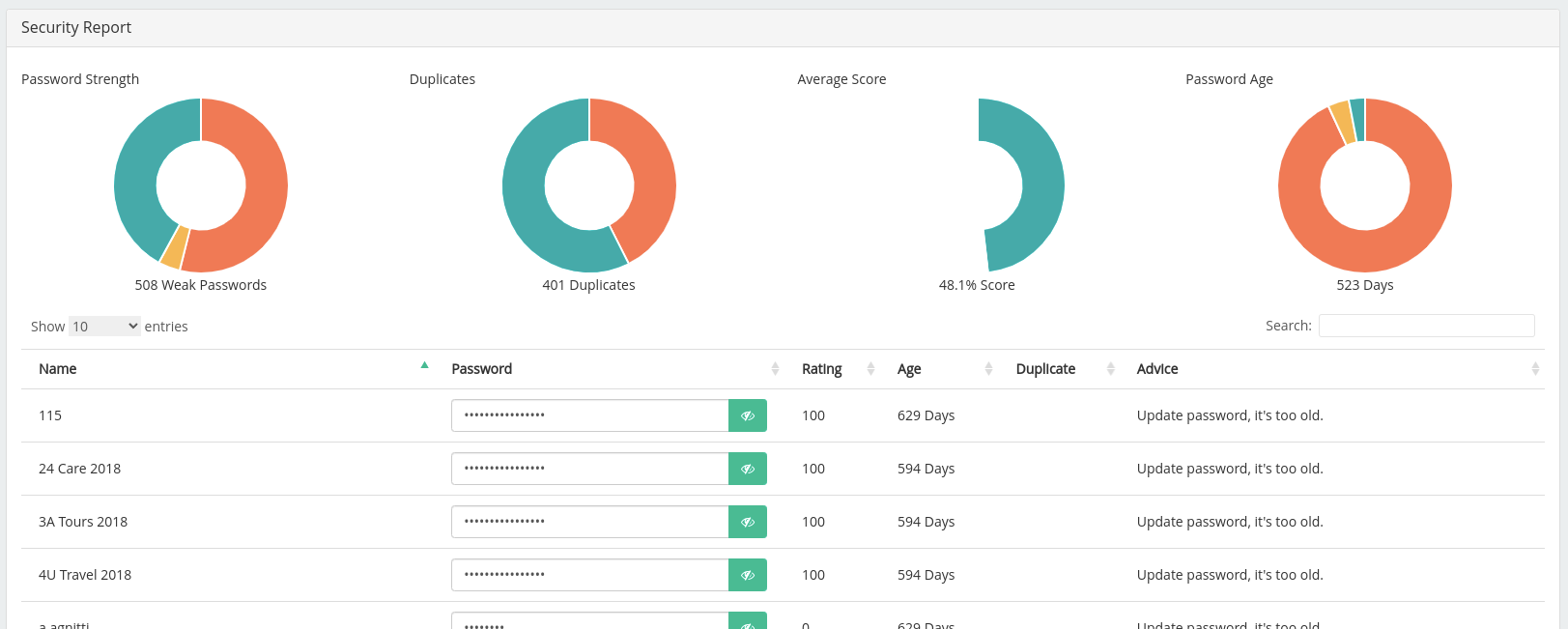
Security Report
The last section we will talk about is the Security Report. We can see here the reports that are sent from the users, how many users are missing a second factor, how many users are missing a recovery code, how many master passwords have been breached, how many master passwords have been used multiple times, how many passwords have been breached and how many passwords have been used multiple times.
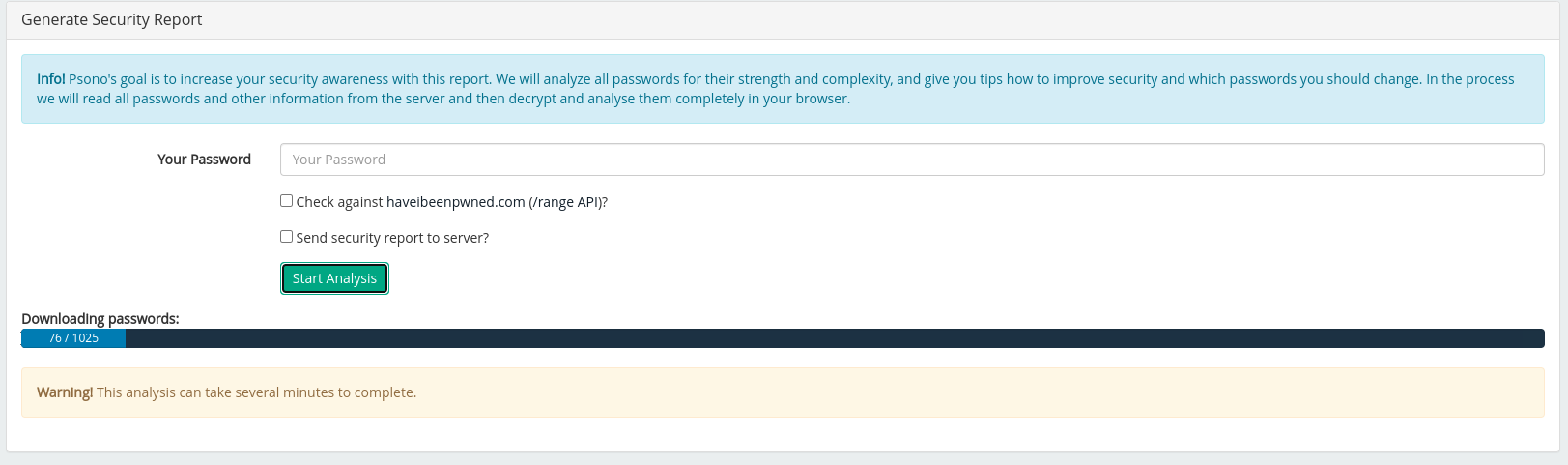
Finally, we can see the result of the report. Not very good, in fact.